Synology SA-17:17 : Surveillance Station - Path Traversal
Impact
An authenticated user with access to Surveillance Station service can access pictures on the whole system.
The impact is limited to picture files.
Proof of Concept
You can easily reproduce this bug by following these steps.
First, we need an account with no permissions to folders and access to the Surveillance Station application.
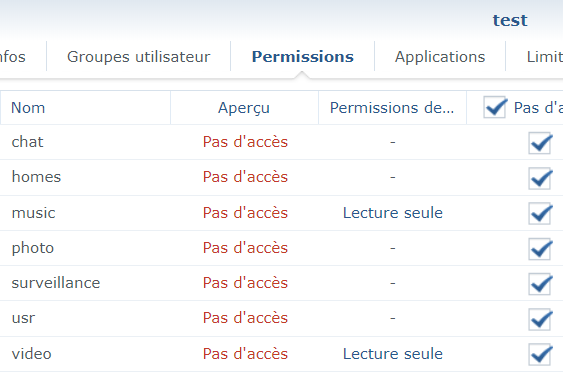
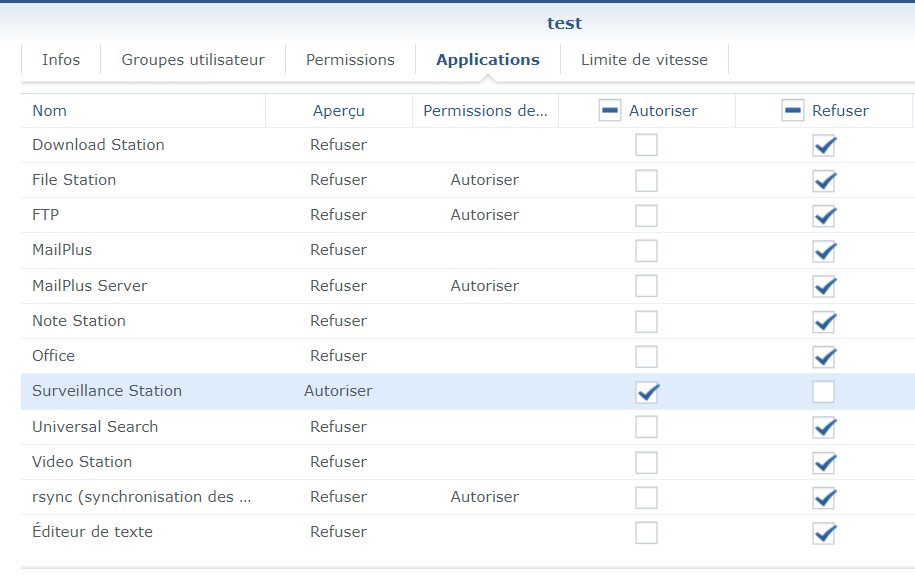
On another account (I use the “synology” account on the demo server) we need to put a picture with default rights.
The vulnerability is present in the user’s profile picture for the Surveillance Station app.
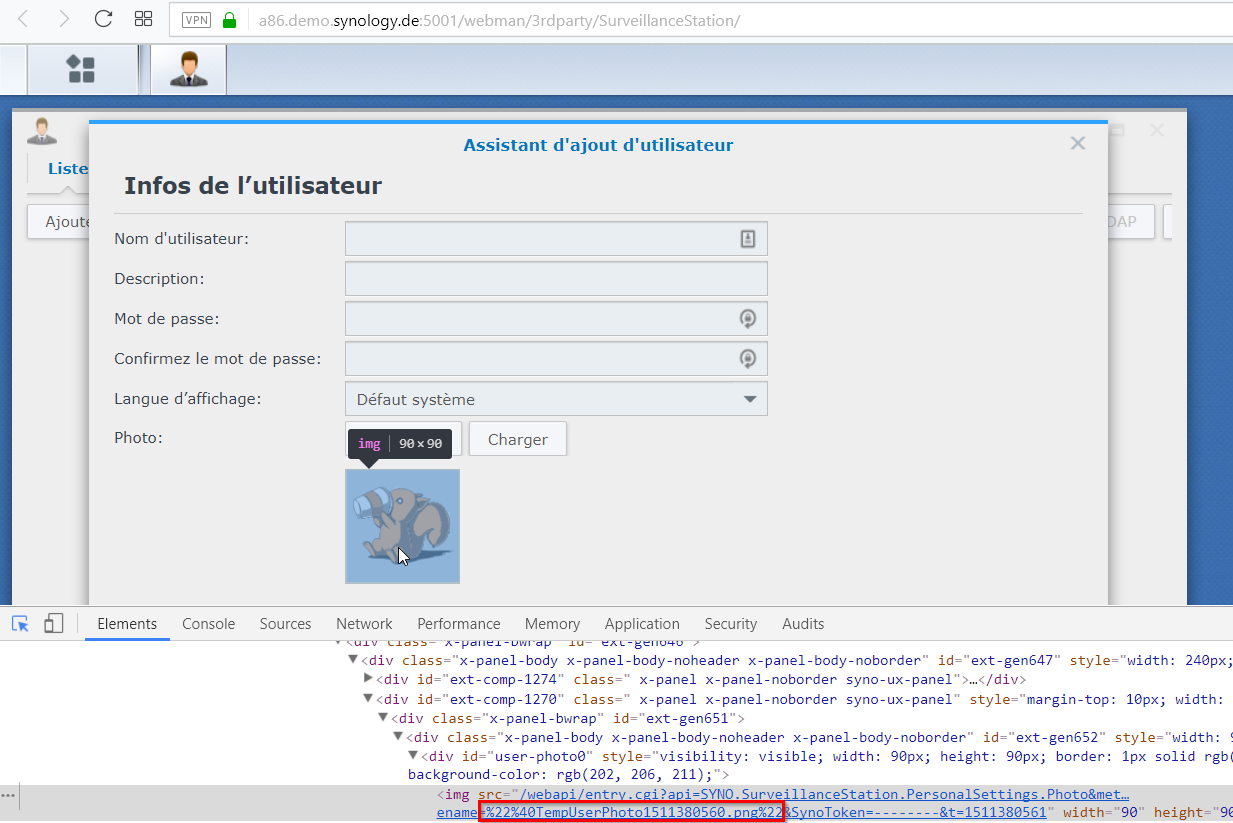
The “filename” parameter allows the attacker to read the pictures in the parent directory.
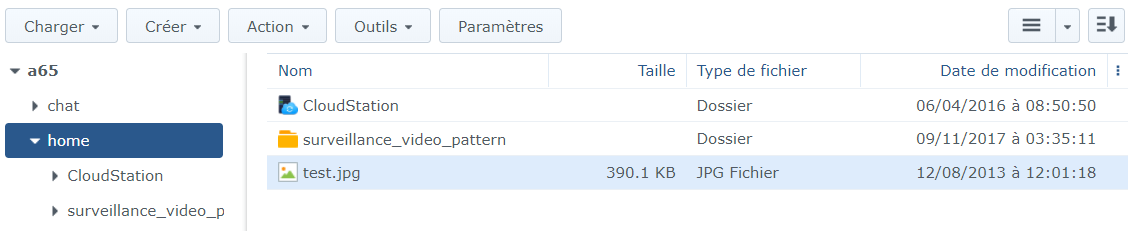
For example, the following link allows getting the “test.jpg” picture in Synology’s private folder.
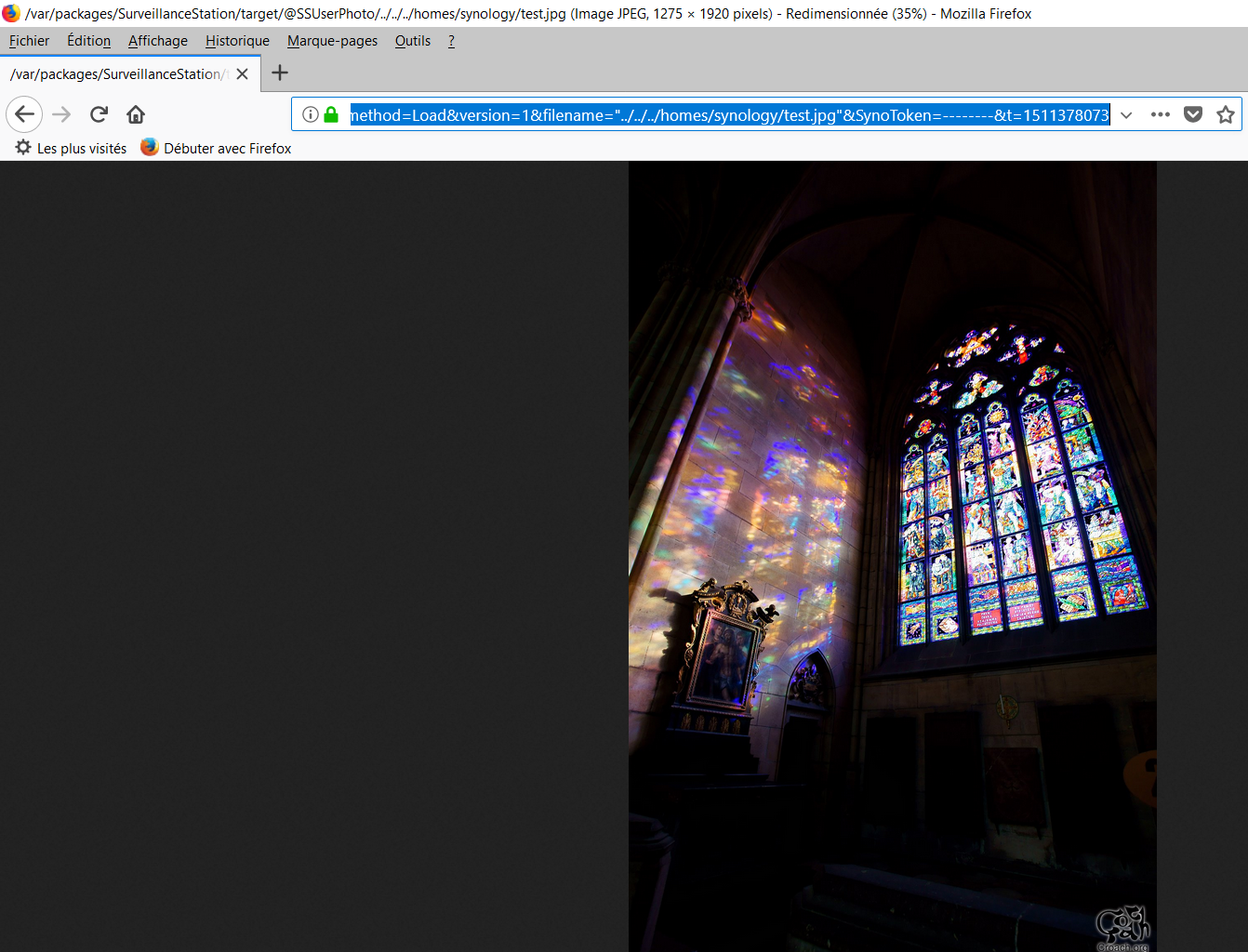
We can also see a full path disclosure on this picture.
Remediation
To fix the vulnerability, you have to verify the file access right before serving it.
You can also limit the Surveillance Station profile picture to the good folder.